Security Network Security: Your Essential Protection Guide
Understanding Security Network Security (It's Not What You Think)
Imagine your company's network as a busy airport. Data packets, like passengers, constantly flow between servers and devices, which act like terminals. Traditional network security was like having a single guard checking tickets at the entrance. This might have sufficed once, but in our interconnected world, it leaves you vulnerable.
Today's threats are more like skilled infiltrators who can bypass simple checkpoints. They might disguise themselves as legitimate data, exploit weaknesses in your system, or even compromise a user account. This calls for security at every point in the network, not just the perimeter.
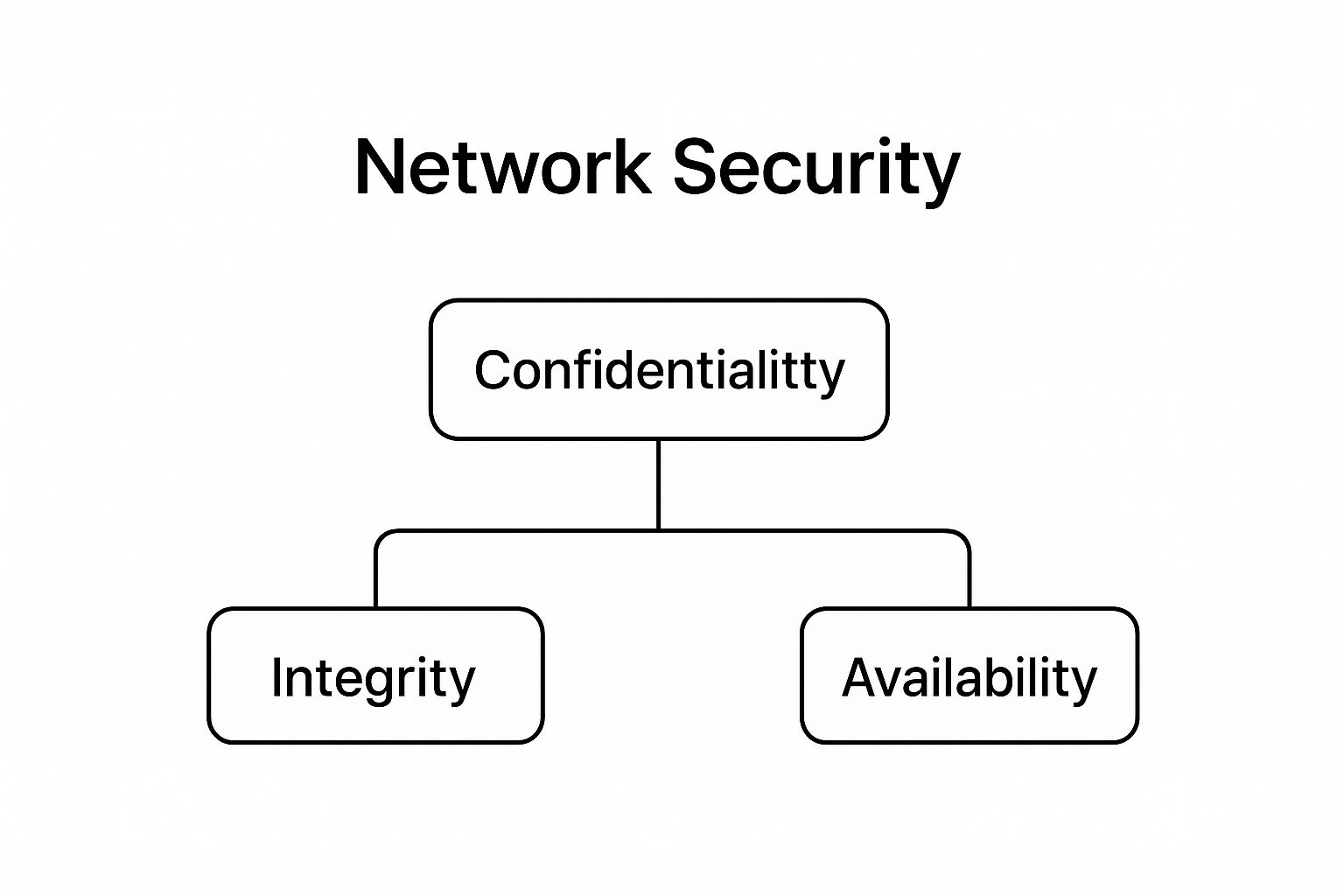
The infographic illustrates the core principles of network security—confidentiality, integrity, and availability, known as the CIA triad. Confidentiality ensures only authorized users access sensitive information. Integrity guarantees data accuracy and prevents tampering. Availability makes sure data and resources are accessible when needed. These elements are interconnected and essential for a strong security posture.
This shift in security thinking fuels the growth of the cybersecurity market, estimated to be between USD 215 billion and USD 301.91 billion in 2025, and projected to reach USD 697 billion by 2035. Discover more insights about cybersecurity market growth This signifies the increasing importance businesses place on protecting their digital assets.
For instance, many companies are adopting a Zero Trust model. This assumes no user or device is inherently trustworthy, even within the network. Every access request is verified, limiting the damage from a potential breach.
Why the "Fortress Mentality" No Longer Works
The old "fortress mentality" of network security focused on building strong perimeter defenses. This approach has several weaknesses in the modern environment:
-
Cloud Computing: With data and applications in the cloud, the network perimeter is no longer clearly defined.
-
Remote Work: Employees accessing the network from diverse locations and devices further complicate perimeter security.
-
Advanced Threats: Sophisticated attackers can bypass traditional firewalls and intrusion detection systems like Snort.
To understand the differences between traditional and modern security approaches, let's examine the following table:
To illustrate the evolving nature of network security, the following table compares traditional and modern methodologies.
Evolution of Network Security Approaches
Comparison of traditional vs modern network security methodologies and their effectiveness
| Security Approach | Primary Focus | Strengths | Limitations | Best Use Cases |
|---|---|---|---|---|
| Traditional (Perimeter-based) | Securing the network boundary | Relatively simple to implement; familiar technologies | Ineffective against insider threats and advanced persistent threats; struggles with cloud and mobile environments | Small, static networks with limited remote access |
| Modern (Zero Trust) | Verifying every access request regardless of location | Strong protection against modern threats; adaptable to cloud and mobile environments | More complex to implement and manage; requires robust identity and access management | Organizations with significant cloud presence, remote workforce, and high security needs |
The table highlights the shift from perimeter-based security to the more comprehensive and adaptable Zero Trust model. This reflects the changing threat landscape and the increasing complexity of modern networks.
Effective network security now demands a layered and dynamic strategy. It needs to address the realities of current work environments and increasingly complex cyber threats. You can find more detailed information in our guide on network security. By moving from reactive to proactive security, organizations can better protect themselves. This means implementing strong security technologies and building a security-conscious culture.
The Real Threats You're Facing (And How They Actually Work)

Today's cyberattacks are less like random acts of digital graffiti and more like carefully planned heists. These campaigns, sometimes brewing for months, pinpoint and exploit the chinks in your network security armor. Think of threat actors as digital spies, meticulously researching their targets, cataloging vulnerabilities, and biding their time for the perfect moment to strike. This section takes you behind the scenes of these real-world attacks, going beyond the theoretical to explore the tactics used against organizations daily.
The Human Element: Your Biggest Vulnerability
Surprisingly, one of the most effective tools for cyber attackers isn't complex code, but human nature. Social engineering, the art of manipulating people, often proves far more effective than brute-force hacking. A carefully crafted phishing email, disguised as a harmless message, can be the gateway to a crippling ransomware attack, potentially costing a company millions. Imagine an employee clicking a link in what looks like a regular email, only to unknowingly download malware that locks down their entire company's data. That's the power of social engineering.
Beyond the Firewall: Modern Attack Vectors
Traditional security measures, like older antivirus software, work by recognizing known malware patterns (think fingerprints at a crime scene). But modern attackers are constantly innovating, crafting new and ever-changing malware that can slip past these defenses. They also exploit weaknesses in legitimate software, like zero-day exploits, rendering traditional firewalls useless. This is why a multi-layered security approach, including behavioral analysis and up-to-the-minute threat intelligence, is so critical.
Inside the Breach: A Slow Burn
Forget the Hollywood image of a fast-paced cyberattack. Many significant breaches aren't quick smash-and-grabs. Often, threat actors gain initial access and then go quiet, sometimes for years. During this period, they meticulously map the internal network, identify crucial systems, and steal valuable data without raising any alarms. This "slow burn" strategy allows them to maximize the damage when they finally decide to act. For a chilling real-world example, check out our article about NotPetya, one of the most devastating cyberattacks in history.
The Real Cost of Inaction
The fallout from a successful cyberattack goes far beyond just financial losses. Damage to reputation, regulatory fines, and legal battles can cripple an organization for years to come. The disruption to business operations, the erosion of customer trust, and the potential exposure of sensitive data can have devastating long-term effects. This emphasizes the urgent need for robust security measures that extend beyond basic perimeter defenses.
What Keeps Security Professionals Up at Night?
The constantly shifting nature of cyber threats is a major source of anxiety for security professionals. The increasing complexity of attack methods, the explosion of connected devices (Internet of Things), and the shortage of skilled cybersecurity professionals all contribute to a challenging security landscape. A proactive, adaptable approach to security is essential, constantly evolving to stay one step ahead. Understanding these real-world threats and their inner workings is the foundation of a strong, resilient security posture.
To illustrate the variety and impact of these threats, let's take a look at some of the most common ones.
The following table provides a comprehensive breakdown of prevalent network security threats, their attack methods, and potential business impact.
Common Network Threats and Impact Analysis
| Threat Type | Attack Method | Target Assets | Potential Impact | Detection Difficulty |
|---|---|---|---|---|
| Malware | Phishing, malicious downloads | Servers, endpoints | Data breaches, system disruption | Moderate to High |
| Ransomware | Phishing, software vulnerabilities | Data, systems | Data loss, financial loss, operational disruption | High |
| Denial-of-Service (DoS) | Flooding network with traffic | Servers, network infrastructure | Service disruption, website downtime | Moderate |
| SQL Injection | Exploiting web application vulnerabilities | Databases | Data breaches, data manipulation | High |
| Phishing | Deceptive emails, websites | User credentials | Identity theft, financial fraud | Moderate |
| Man-in-the-Middle (MitM) | Intercepting communication | Data in transit | Data breaches, eavesdropping | High |
As you can see, the consequences of these attacks can range from disruptive to devastating. Early detection and prevention are key to minimizing the impact of these threats.
Building Security That Actually Works In Practice

Let's face it: a shiny new security system doesn't guarantee actual security. Imagine a fortress with state-of-the-art locks, but the guards keep leaving the keys under the welcome mat. That's what happens when security measures clash with real-world practices. If a system is too complex, people will find workarounds, often creating bigger vulnerabilities than the ones you're trying to fix. Effective security considers human behavior and aims to make secure practices easy and intuitive.
Zero Trust: Beyond the Buzzword
Zero trust is a significant change in how we think about security. Instead of assuming everything behind the firewall is safe, zero trust verifies every single access request. Think of it like a building with security checkpoints on every floor, not just at the front door. Whether you're inside or outside the network, every attempt to access a resource is scrutinized. This "never trust, always verify" approach minimizes the damage a potential breach can cause, acting as a series of internal checks and balances within your digital workspace.
Practical Implementations: Balancing Security and Usability
Implementing zero trust successfully requires a delicate touch. Security measures that are too restrictive can backfire. Imagine a file-sharing system so complex that employees resort to using personal email to share sensitive documents. Suddenly, your data is outside your control entirely. The trick is to find the sweet spot: strong security without hindering productivity. Multi-factor authentication (MFA), for instance, adds a robust layer of security without making logins overly complicated.
Network Segmentation: Dividing and Conquering
Network segmentation is another key aspect of practical security. It’s like dividing your house into separate rooms with different levels of access. If someone breaks into the living room, they can’t automatically get into the vault where you keep your valuables. By dividing your network into smaller, isolated sections, you limit the blast radius of a breach. If one segment is compromised, the attacker can't easily move laterally to other, more sensitive areas. This segmentation should reflect your business structure, separating crucial systems and sensitive data from less critical areas.
Monitoring That Matters: Actionable Intelligence
Good monitoring is essential. But a constant barrage of alerts can overwhelm security teams, leading to alert fatigue. It's like having a smoke detector that goes off every time someone makes toast. Eventually, you'll just start ignoring it. Instead of a flood of notifications, focus on actionable intelligence. This means prioritizing alerts based on the actual risk they pose, connecting events from various sources, and giving analysts the context they need to understand what's happening. This lets security teams focus on real threats, improving response times and minimizing potential damage. For a deeper look into securing the devices on your network, check out our guide on endpoint management. This forms a crucial part of a comprehensive security strategy.
By focusing on these practical elements – understanding how people work, applying zero trust principles thoughtfully, segmenting the network strategically, and prioritizing actionable intelligence – you can build security that's both effective and sustainable. These aren't just best practices; they’re the foundation of a robust and adaptable security posture.
Security Technologies That Work Together (Not Against Each Other)
The biggest mistake organizations make is treating security tools as separate entities. Instead of a cohesive defense, they end up with a scattered collection of tools. Think of effective network security as a well-coordinated orchestra. Each instrument plays a distinct role, but the real power comes from their combined performance under a conductor. This integrated approach is key to building a strong defense.
The Power of Integration: A Unified Defense
Top organizations understand that firewalls, intrusion detection systems (IDS), endpoint protection, and Security Information and Event Management (SIEM) platforms must work as one. For example, a next-generation firewall (NGFW) might detect unusual traffic and immediately alert the SIEM platform. The SIEM then cross-references this alert with data from other sources, such as endpoint security logs, to get a complete view of the potential threat. This interconnected approach allows security teams to respond quickly and stop threats before they cause significant damage. Imagine your security system as a high-performance engine, with every part contributing to its overall effectiveness. This coordination allows for rapid identification and response to potential breaches, minimizing disruption and data loss.
Avoiding the Integration Pitfalls: Bridging the Gaps
Many security implementations fail because of poor integration. This often creates security gaps, where tools operate in silos, failing to share critical information. It’s like a football team where the offense and defense aren't communicating – a recipe for disaster. For instance, if your endpoint protection finds malware but doesn't tell the firewall, the infected device could continue communicating with malicious servers, spreading the infection. This lack of communication creates an opening for attackers. Additionally, poorly integrated systems can lead to alert fatigue, overwhelming security teams with a flood of unimportant notifications, making it harder to spot real threats. The importance of these considerations is underscored by the significant role North America, especially the U.S., plays in the cybersecurity market. In 2024, the U.S. cybersecurity market was valued at USD 77.2 billion and is expected to reach USD 236.04 billion by 2034. Find more detailed information on cybersecurity market trends. This rapid growth emphasizes the rising investment in security and the crucial need for effective implementation.
The Evolving Role of Security Technologies
Security technologies are constantly evolving to keep pace with new threats. NGFWs have gone beyond basic traffic filtering, adding features like deep packet inspection and intrusion prevention systems (IPS) to actively analyze network traffic for malicious activity. Behavioral analytics are also changing how we detect threats, using machine learning algorithms to spot unusual user and device behavior. This helps security teams find and address threats that traditional, signature-based systems might miss. For example, if a user suddenly starts accessing files they’ve never accessed, the system can flag this as potentially suspicious and send an alert.
Building Your Security Stack: A Strategic Approach
Building a strong security posture requires a strategic approach to choosing and integrating security technologies. Not all security technologies work well together. Some might conflict or overlap, while others complement each other. It’s important to know each tool's strengths and weaknesses and how it fits into your overall security strategy. This means thinking carefully about your specific needs, picking technologies that address them effectively, and making sure they integrate smoothly to form a unified defense. Like a conductor carefully selecting and arranging instruments for a symphony, a security architect must choose and integrate tools to create a harmonious and effective security system. This layered approach, combining various technologies working together, is essential for protection against today’s complex threats.
Monitoring And Response That Makes The Difference

Many organizations face a flood of security alerts, often burying the important signs of real danger. Effective network security monitoring is about separating everyday quirks from genuine attacks. Think of a detective sorting through evidence – they know which clues matter and which are distractions.
This section explores how to create a security monitoring and response system that gives you useful information without overwhelming your team.
Identifying Real Threats: The Art of Threat Detection
Imagine a security team drowning in thousands of daily alerts. Most are false positives – harmless glitches mistaken for attacks. But hidden within this noise could be subtle signs of a real breach. How do you find a needle in a haystack?
The answer lies in understanding what "normal" looks like. By establishing baselines of typical network activity, security teams can spot unusual deviations that need investigation. This means analyzing things like network traffic, user behavior, and system logs to build a clear picture of regular operations.
For example, a sudden jump in login attempts from unexpected places could signal a brute-force attack. Likewise, unusual data transfers to outside servers might suggest data theft. These anomalies, compared against the established baselines, offer vital clues.
Building Effective Monitoring Capabilities
Effective monitoring isn't about gathering all the data; it's about gathering the right data. Focus on metrics that really point to a problem, such as strange login activity, unexpected file access, and questionable network connections.
Tools like Security Information and Event Management (SIEM) platforms can help. SIEM platforms collect and analyze data from many sources, offering a complete overview of your security situation. This allows security teams to connect the dots and spot potential threats more easily.
Also, consider behavioral analytics. These systems use machine learning to find unusual behavior that traditional systems might miss. They can pick up on subtle changes in user activity, system performance, and data access that might indicate an emerging attack.
Incident Response: Minimizing Damage and Recovery Time
When an attack happens, a clear incident response plan is essential. This plan should outline steps for containing the breach, eliminating the threat, and getting back to normal. It's like a fire drill – everyone knows their role and what to do in an emergency.
A solid incident response plan includes:
-
Clear communication channels: Who to contact, and how.
-
Containment strategies: How to isolate affected systems and limit further damage.
-
Eradication procedures: How to remove the threat and fix affected systems.
-
Recovery steps: How to get systems back online and working normally.
Post-Incident Analysis: Learning From Mistakes
After an incident, a detailed post-incident analysis is vital. This involves reviewing what led to the attack, finding weaknesses that were used, and taking steps to prevent future problems. Think of it like reviewing game film – you analyze what went wrong and figure out how to improve.
Often, the most valuable lessons come not from the initial response, but from carefully studying what happened afterward. This analysis helps organizations learn from their mistakes, improve their security, and become more resilient. By constantly refining their monitoring and response, organizations can stay ahead of evolving threats and protect what matters most.
Making Enterprise Security Work Without Breaking Everything
Imagine trying to upgrade the security systems of a massive, bustling airport while planes are constantly landing and taking off. That's the challenge of implementing network security in a large enterprise. It requires more than just technical skill; it demands a deep understanding of the business itself. You need to keep operations running smoothly while making critical changes.
This section explores the practicalities of enterprise security—how to achieve robust protection without disrupting the flow of business. We'll look at real-world scenarios and learn from companies who've successfully strengthened their defenses without sacrificing efficiency.
Navigating the Complexities of Business-Critical Systems
Think of an enterprise's business-critical systems as its central nervous system. These systems need to be always on, yet they're often built on older technology that can be tricky to update. Making security changes without bringing everything to a screeching halt requires careful planning and specialized techniques.
Think of it like changing a tire on a moving car: Timing and coordination are everything. Rolling updates, where changes are applied incrementally, are one strategy. Another is blue-green deployments, where a duplicate environment is created to test updates before switching over the live system.
This diagram from the Wikipedia page on Computer Network Security offers a simple visualization of how security layers interact. Notice the layered approach: multiple security mechanisms, from physical barriers like fences to data encryption, work together. This highlights the importance of a holistic security strategy.
Securing the Hybrid Cloud: A Multi-Platform Challenge
Many businesses today operate in a hybrid cloud environment, with data and applications spread across on-premises servers, private clouds, and public cloud platforms like AWS or Azure. Securing this diverse landscape presents unique challenges.
Each platform has its own security features, so creating a consistent level of protection requires careful integration. This means using tools that can monitor all platforms, establishing unified security policies, and coordinating security efforts between teams.
Adapting Security Policies for the Remote Work Era
With more people working remotely, the way we connect to corporate networks has changed dramatically. Employees now access systems from a variety of locations and devices, increasing the potential points of attack.
Securing this new normal requires strong access controls, robust multi-factor authentication (MFA), and effective endpoint security on every device. It also means training employees on security best practices and building a culture of security awareness.
Integrating Security into DevOps: Speed and Security
Integrating security directly into the software development process (often called DevSecOps) is essential for maintaining both speed and safety. This involves automating security tests and incorporating security tools within the development pipeline.
Catching vulnerabilities early in the development cycle prevents them from becoming expensive problems later on. This proactive approach also allows teams to respond more quickly to potential threats.
Balancing Compliance and Efficiency: A Delicate Dance
Businesses face a web of regulations like GDPR, HIPAA, and PCI DSS. These regulations often mandate specific security measures, adding another layer of complexity. The key is to meet these requirements without sacrificing the ability to move quickly and adapt.
Choosing tools that automate compliance reporting, integrating compliance checks into existing processes, and designing security architecture with compliance in mind can significantly simplify audits and demonstrate a commitment to security.
Building Scalable Security Programs
As companies grow, so do their security needs. A successful security program must be able to scale and adapt along with the business. This requires flexible security frameworks, cloud-based solutions that can expand on demand, and a culture of continuous improvement.
By embracing these strategies, organizations can build robust security systems that protect their valuable assets without hindering their growth and innovation. This allows them to strike a balance between strong protection and the flexibility required in today's dynamic business world.
Staying Ahead of Tomorrow's Security Challenges
The future of network security isn't a distant prophecy; it's unfolding right now. Organizations that will flourish in the coming years are those that can quickly adjust to the ever-changing threat landscape. This means anticipating how new technologies will influence both offensive and defensive strategies.
The AI Arms Race: Automated Attacks vs. Autonomous Defenses
Artificial intelligence (AI) is a powerful tool that can be used for good or bad. Attackers leverage AI to automate attacks, making them faster, more efficient, and stealthier. Think of it like a swarm of AI-powered robots constantly probing your defenses for vulnerabilities. But AI also empowers defenders, enabling autonomous defense systems. These systems can analyze huge amounts of data, spot threats in real-time, and even neutralize them without human intervention. This creates a continuous back-and-forth, with each side developing increasingly advanced AI tools.
Imagine a chess match where both players use AI to predict and counter each other’s moves. That’s the essence of the AI arms race in security.
Quantum Computing: The Encryption Enigma
Quantum computing presents a serious threat to current encryption methods. Most encryption relies on complex math problems that are difficult for regular computers to solve. Quantum computers, however, could potentially break these codes, rendering our current security useless. It’s like having a skeleton key that opens any lock. This means we need to develop new, quantum-resistant encryption algorithms to safeguard data in the future. This represents a vital challenge for the future of security, requiring substantial research and development.
The IoT Explosion: Expanding the Attack Surface
The Internet of Things (IoT) is rapidly expanding, connecting everything from smart appliances to critical infrastructure. Each connected device represents a new potential entry point for attackers. Imagine your network as a house, and every IoT device is a window or door. The more connected devices you have, the more potential openings there are for intruders. This massive growth of the attack surface complicates network security and demands new strategies that can manage the sheer quantity and variety of connected devices.
Preparing for the Unknown: Building Adaptable Security
The future of security is uncertain, but we can prepare. This means building agile security programs that can adjust to new threats and technologies as they emerge. It also means investing in security awareness training for employees. After all, people are often the weakest link in the security chain. Fostering a security-conscious culture, where everyone understands their part in protecting the organization, is crucial. This involves regular training and awareness programs, not just one-off events.
Strategic Planning for Future Security
Organizations require a strategic planning framework for security. This framework should direct investments, prioritize security initiatives, and align them with business objectives. It also means recognizing the skills needed for the future security environment and investing in training and development programs in areas like AI security, cloud security, and data privacy. By thinking strategically and adapting to change, organizations can establish robust security postures that can withstand future challenges.
Want to delve deeper into building a strong and adaptable security posture for your organization? Explore the resources and expert insights available at DATA-NIZANT, your guide to the world of data science, AI, and digital infrastructure.



