Mastering Endpoint Management: Securing and Controlling Devices Across the Enterprise: Endpoint Management Tips: From Chaos to Control
What Endpoint Management Really Means For Your Organization
Imagine conducting an orchestra where half the musicians are playing different tunes, in different keys, and some are even hidden from view. Managing devices without proper endpoint management can feel just as chaotic. It’s not simply about knowing where your laptops and smartphones are; it’s about orchestrating all devices into a secure, cohesive unit.
This involves a centralized system that lets you see, control, and protect every device connecting to your network. Picture a small business with 20 laptops. Endpoint management enables their IT team to install software updates, enforce security policies, and fix problems remotely on all devices at once. This simplifies operations and ensures smooth running. Tools like Tanium Essentials empower even lean IT teams to patch vulnerabilities, enforce security baselines, and remediate issues — all from a single console, in real time.
Now, imagine a large enterprise managing thousands of devices, including smartphones, tablets, and IoT sensors. Without robust endpoint management, this becomes a logistical nightmare. This underscores why a solid strategy is crucial—not just for IT, but for the entire organization’s security. Endpoint management helps shift from reactive problem-solving to proactive device governance. Tanium, used by some of the world’s largest enterprises, delivers real-time visibility and control across millions of endpoints — whether they’re on or off the corporate network.
This increasing need isn’t just anecdotal. The sheer volume of devices connecting to company networks has made endpoint management essential. Market research shows the endpoint security market—a close relative of endpoint management—is projected to grow from its 2020 value to $18.6 billion by 2027, at a CAGR of 5.9%. However, for comprehensive solutions covering not just security but also device management, remote access, and policy enforcement, growth is even faster. Discover more insights about endpoint management growth. This growth highlights the rising importance of effective endpoint management in our interconnected business world.
Why Endpoint Management Is More Than Just IT Convenience
Traditional methods like separate antivirus software and manual updates can’t handle the demands of today’s flexible work environments. Updating software on hundreds of devices individually would be incredibly time-consuming. Endpoint management automates this, saving significant time and effort. You might be interested in: data visualization best practices. This shift from manual to automated management is about more than convenience; it’s about proactively reducing security risks and ensuring business continuity. Endpoint management provides essential control and visibility in an increasingly complex technological world.
Why Organizations Are Racing To Adopt Endpoint Management

The rise of remote work, combined with increasingly complex cyberattacks, has put immense pressure on IT departments. Traditional IT strategies are struggling. Imagine trying to protect a castle with walls designed for a small village – that’s the challenge IT faces. The “village” of connected devices – laptops, smartphones, even IoT sensors – is constantly expanding, creating a much larger target for attacks. This growing complexity demands a new approach: endpoint management.
The Urgency of Effective Endpoint Management
Many organizations are realizing that endpoint management is no longer optional, but essential for survival. The true costs of weak endpoint security are often hidden, like the productivity drain of slow, outdated software or the constant need for IT troubleshooting. These small issues add up and significantly impact the bottom line. Imagine a company of 100 employees losing just 15 minutes each day to IT problems. That lost time translates directly into lost revenue.
Remote work has also blurred the lines between personal and work devices, opening up new security vulnerabilities. A compromised personal device accessing company data could expose sensitive information and disrupt operations. This requires a new level of security that extends beyond the traditional office network.
The Rising Adoption of Endpoint Management Solutions
The growing need for robust endpoint security is reflected in the booming unified endpoint management (UEM) market. In 2024, the market was valued at $13.35 billion. By the end of 2025, it’s projected to reach $17.24 billion, a compound annual growth rate (CAGR) of 29.1%. Discover more insights into this remarkable growth. This explosive growth highlights how important endpoint management has become.
Why Traditional IT Approaches Are Falling Short
Traditional IT management, often reactive and fragmented, just isn’t designed for today’s interconnected world. Managing devices individually with separate antivirus software and manual updates is like trying to fight a wildfire with a garden hose. Endpoint management provides the firetruck: a central platform to proactively address security threats, deploy software updates, and manage devices efficiently.
This proactive approach saves time and resources, reduces risks, boosts productivity, and allows organizations to embrace the benefits of a connected workforce. Moving from reactive to proactive management is key to staying ahead and maintaining a competitive edge.
Building Your Endpoint Management Foundation That Actually Works
Every successful endpoint management strategy starts with understanding the basics. It’s like building a house – you need a solid foundation before you start adding the fancy features. We’ll explore the core parts of effective endpoint management, covering everything from initially finding and listing devices to enforcing policies and making sure everyone follows the rules.
Essential Components of a Robust Endpoint Management System
Effective endpoint management isn’t just about controlling devices, it’s about building a complete management system. These are the essential building blocks:
- Device Discovery and Inventory: First, you need to know what devices are on your network. This means automatically identifying and cataloging every device, from laptops and smartphones to tablets and even Internet of Things (IoT) devices.
- Software Deployment and Patch Management: Keeping software updated is key for both smooth operation and strong security. Endpoint management automates this, ensuring consistent software installations and timely security patches across all devices.
- Policy Enforcement and Configuration Management: Setting and enforcing security policies is crucial. This includes things like password requirements, who can access what, and encrypting sensitive data. Endpoint management helps you apply these rules consistently.
- Compliance Monitoring and Reporting: Regularly checking if devices are following the rules is essential for maintaining good security. Endpoint management gives you the tools to track this and create reports.
- Remote Monitoring and Troubleshooting: Being able to check device performance, diagnose problems, and help users remotely is a major advantage, saving time and resources.
These components work together to build a single, unified management system. This system improves security, simplifies IT tasks, and empowers your employees to work effectively. It’s a big step up from simply controlling devices and moves towards complete endpoint governance.
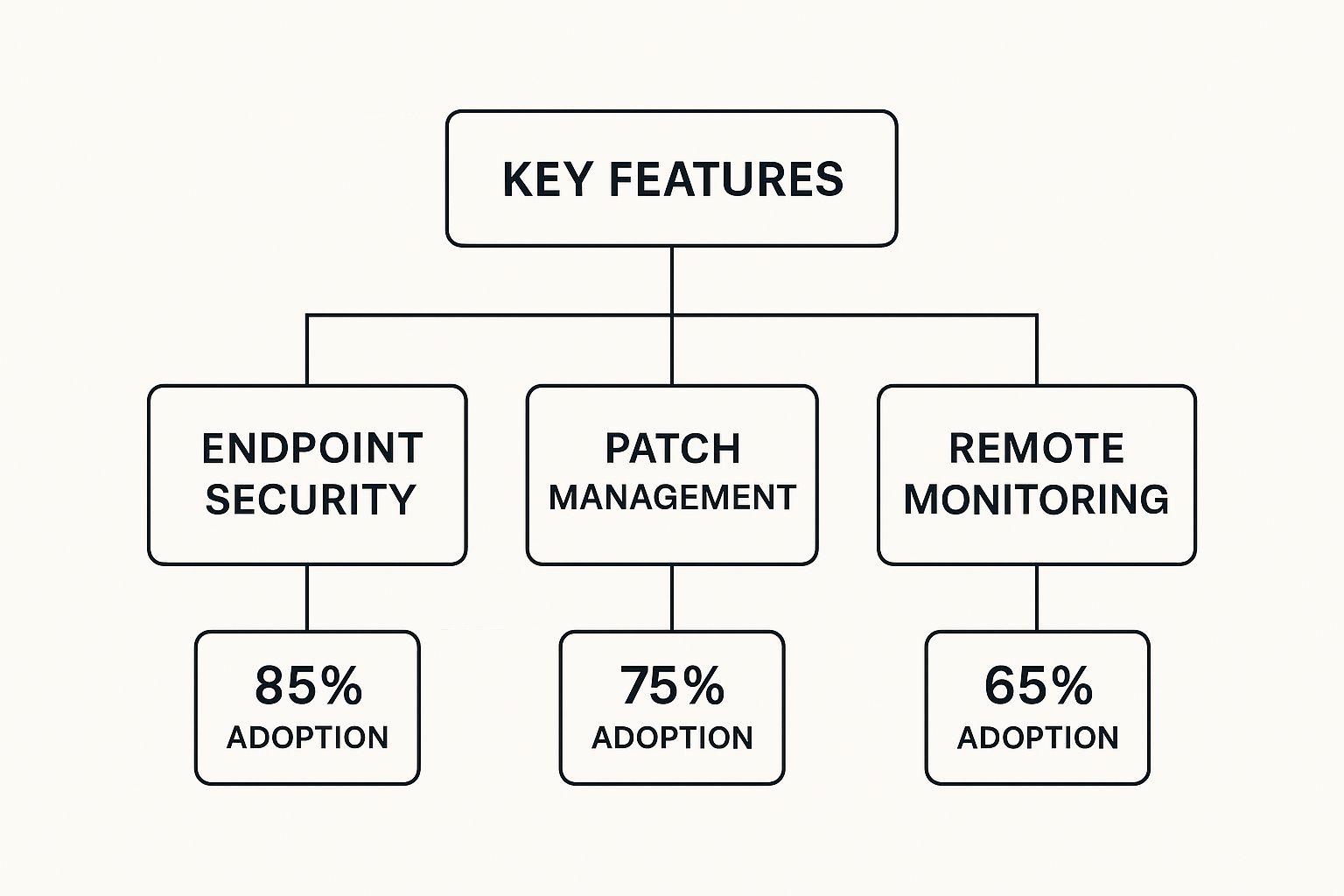
The infographic above shows how often different endpoint management features are used in modern solutions. Endpoint Security is the most common at 85%, followed by Patch Management at 75%, and Remote Monitoring at 65%. This tells us that security is the top priority, but proactive patching and remote monitoring are also becoming increasingly important.
To help you understand the different levels of endpoint management solutions, let’s look at a comparison table:
Essential Endpoint Management Components Comparison
This table compares core endpoint management capabilities and shows how they impact your business across different types of solutions.
| Component | Basic Solutions | Advanced Platforms | Business Impact |
|---|---|---|---|
| Device Discovery and Inventory | Manual or limited automated discovery | Automated discovery and real-time tracking | Improved visibility and control over devices |
| Software Deployment and Patch Management | Basic software deployment, often manual patching | Automated software deployment and patching | Reduced security risks and improved productivity |
| Policy Enforcement and Configuration Management | Limited policy enforcement | Granular policy control and automated configuration | Enhanced security posture and compliance |
| Compliance Monitoring and Reporting | Basic reporting capabilities | Comprehensive reporting and analytics | Better insights into device compliance and potential issues |
| Remote Monitoring and Troubleshooting | Limited remote access | Robust remote monitoring and troubleshooting tools | Faster issue resolution and reduced downtime |
As you can see, more advanced platforms offer significantly more control, automation, and insight, leading to better security and operational efficiency.
Prioritizing Core Capabilities vs. Add-ons
Not all endpoint management features are equally important. Some are must-haves, while others are optional extras. For example, basic device tracking and software installation are fundamental. More advanced features like behavioral analysis or threat hunting might be something you add later. Knowing the difference helps you build a solution that fits your budget and tackles your most urgent needs first. This makes your endpoint management foundation strong and flexible for future growth. You can start with the core components and gradually add more advanced features as your organization expands. This smart approach avoids spending money on things you don’t need yet, while still establishing a strong foundation for endpoint security and management.
Cloud Versus On-Premise: Making The Right Deployment Choice

Picking the right way to deploy your endpoint management solution is a big decision. Think of it like choosing the foundation for your house: it needs to be solid and right for your specific needs. A simple pros and cons list isn’t enough. You need to truly understand what each approach means in practice.
Cloud Deployments: Riding the Wave of Adoption
Cloud-based endpoint management has skyrocketed in popularity, and for good reason. Imagine having a property manager handling all your building maintenance. That’s what the cloud offers: automatic updates, the ability to easily scale, and a lot less hassle. This frees up your IT team to focus on bigger-picture projects instead of getting bogged down in routine maintenance. Cloud solutions also offer quicker deployment and simpler access for remote workers—a must-have in today’s world.
This move to the cloud isn’t just a trend. The unified endpoint management (UEM) market is expected to see explosive growth, fueled by cloud adoption. Between 2025 and 2029, the global UEM market is projected to go from a multi-billion dollar industry to a whopping $111.62 billion by 2029, with a compound annual growth rate (CAGR) of 58%. This incredible growth highlights the increasing dominance of cloud-based endpoint management. You can learn more about the growing UEM market.
On-Premise: Control and Customization
On-premise solutions give you more direct control over your data and systems. This is a big draw for organizations with strict compliance rules or those in heavily regulated industries. It’s like owning your own home: you’re in charge of all the renovations and security. However, on-premise deployments require a substantial initial investment in hardware and ongoing upkeep, which can be a roadblock for some. If you’re considering this route, you might also be interested in resources on cloud cost optimization.
Hybrid Approaches: Bridging the Gap
Hybrid approaches offer a blend of both worlds. Think of it like owning a vacation home – you get some of the perks of ownership without all the responsibility. Organizations can keep sensitive data on-premise while taking advantage of the cloud’s scalability and flexibility for other functions. This allows for a customized approach that addresses specific security and control needs while still benefiting from the advantages of the cloud.
Navigating Integration Challenges and Choosing the Right Path
Integrating new endpoint management solutions can be complex, no matter how you deploy them. It’s essential to carefully consider your organization’s particular needs, including security requirements, compliance regulations, and plans for future growth. Planning ahead can help you avoid expensive mistakes and ensure a smooth transition. Instead of getting hung up on a checklist of features, focus on finding a solution that truly aligns with your overall business strategy. This strategic thinking maximizes your return on investment and sets you up for success in the long run.
Implementation Strategies That Deliver Real Results

This screenshot gives you a glimpse into the world of Mobile Device Management (MDM), a key part of endpoint management. Notice how it highlights important functions like security management, app management, and device enrollment. It’s a good visual reminder that endpoint management is much more than simply tracking devices—it’s about comprehensive control and security.
Implementing endpoint management successfully isn’t just about picking the right software. It’s about careful planning and execution. Think of it like planning a road trip. You wouldn’t just hop in the car and start driving, would you? You’d map your route, plan gas stops, and think about possible delays. A successful endpoint management implementation needs that same kind of roadmap.
Planning For Success: A Phased Approach
A phased approach brings structure and lets you adjust as you go. Start with a pilot program, focusing on a small group of users and devices. This lets you test the system, find any hidden issues, and refine your processes before a full rollout. For instance, start with one department or team to get some experience and gather feedback. This controlled rollout helps minimize disruption and makes for a smoother transition.
Engaging Stakeholders: Getting Buy-In From The Start
Getting everyone on board—from IT to end-users—is crucial. Clearly communicate the benefits of endpoint management. Address concerns, provide training, and remember that user resistance can quickly derail a project. Imagine trying to implement a new traffic system without telling drivers—chaos would ensue! Similarly, educating users about the new endpoint management system and how it benefits them is key. Make sure they understand the “why,” and they’re much more likely to cooperate.
Addressing Technical Challenges: Anticipating The Unexpected
Technical hiccups are bound to happen. Expect potential integration issues, compatibility problems, and network limitations. Having a plan B—like a rollback strategy or alternative deployment methods—can save you time and headaches. For example, having a dedicated support team during rollout can address user issues quickly and efficiently. This proactive approach minimizes disruptions and user frustration.
Measuring Progress: Tracking Key Metrics
Define clear metrics to track progress and show the value of your efforts. These metrics could be things like fewer help desk calls, better security compliance, or faster software deployments. These measurable results justify the investment in endpoint management and demonstrate its impact. These metrics should align with overall business goals, like increased productivity or reduced security risks.
Ongoing Optimization: Continuous Improvement
Endpoint management isn’t a “set it and forget it” project. It’s an ongoing process. Regularly review your system, gather feedback, and make adjustments. The tech world is always changing, so your endpoint management strategy needs to be flexible and adaptable. This ensures your system stays effective and continues to meet your organization’s evolving needs. Regularly reviewing and updating your strategy is crucial for strong security and efficient device management. This lets you tackle new challenges, adapt to changing technologies, and maximize the benefits of your investment.
To illustrate a typical implementation timeline, the table below outlines the key phases, their durations, the main activities involved, and the metrics used to measure success.
Endpoint Management Implementation Timeline
| Phase | Duration | Key Activities | Success Metrics |
|---|---|---|---|
| Planning & Assessment | 2-4 weeks | Define scope, gather requirements, assess current infrastructure | Completion of project plan, stakeholder alignment |
| Pilot Deployment | 4-6 weeks | Deploy endpoint management solution to a small group of users and devices | User feedback, identification of technical issues |
| Full-Scale Rollout | 8-12 weeks | Deploy solution to all users and devices, provide training and support | User adoption rate, reduction in help desk calls |
| Ongoing Optimization | Continuous | Monitor system performance, gather feedback, make adjustments | Improved security compliance, faster software deployments |
By following a structured approach, engaging stakeholders, addressing technical challenges, and committing to continuous improvement, organizations can achieve real results with endpoint management, transforming devices from potential liabilities into valuable assets.
Turning Endpoints Into Your Security Advantage
Let’s shift our perspective on endpoints. Instead of viewing them as weak points, think of them as the first line of defense in your security setup. Modern endpoint management has the power to change these devices from potential liabilities into proactive security assets. They can automatically detect, prevent, and even respond to threats. This isn’t some futuristic dream; it’s how businesses are operating today with effective endpoint management.
Integrating Endpoint Management With Your Broader Security Strategy
Imagine your security strategy is a castle. Historically, we’ve focused on reinforcing the outer walls – firewalls and perimeter security. But what happens when someone sneaks past those defenses? Endpoint management is like having guards stationed inside, ready to respond to threats immediately. It works alongside your overall strategy, providing an essential inner layer of defense.
Let’s say an employee clicks a phishing link. Without endpoint management, malware could spread like wildfire. But with a robust system in place, the threat can be contained and neutralized before it causes any real harm. This shift from reacting to threats to proactively stopping them is a real game-changer.
This integration is also key for putting zero-trust principles into action. Zero trust operates on the assumption that no device or user is inherently safe. Endpoint management enforces this by continuously verifying devices, restricting access based on real-time risk assessments, and providing constant monitoring. This empowers your company to embrace flexible and remote work arrangements without compromising security.
Automating Threat Response: Handling Threats While You Sleep
Picture security guards patrolling your network around the clock, automatically handling threats even while you’re asleep. That’s the potential of automated threat response. Endpoint management platforms can be set up to quarantine infected devices, block harmful traffic, and even automatically patch vulnerabilities without any human intervention. This proactive approach minimizes the damage from attacks and frees up your IT team for more strategic work.
This automation goes beyond basic responses. Advanced features like behavioral analysis and threat hunting turn raw endpoint data into usable security intelligence. Imagine a detective spotting suspicious activity on a security camera – that’s similar to what behavioral analysis does. It detects unusual device behavior, which could point to a hidden attack. This enables security teams to identify and address threats before they escalate. You might find this relevant: Endpoint security topics we’ve covered.
🗒️ Note: With Tanium’s automated response playbooks, threats are isolated, remediated, and audited in real time — a critical capability for enforcing Zero Trust principles at scale.
Strengthening Your Entire Security Posture: From Devices to Data Centers
Effective organizations understand that endpoint management isn’t just about individual devices; it’s about bolstering their entire security setup. By monitoring and managing all endpoints, you get valuable data about network activity, user behavior, and emerging threats. This information can then be used to improve security policies, use resources more efficiently, and even anticipate future attacks.
Think of each endpoint as a sensor gathering crucial security information. Endpoint management combines this data to give you a complete view of your security landscape. This improved visibility lets you proactively find vulnerabilities and strengthen your defenses across your entire system, from individual devices to the data center. Endpoint management isn’t just a tool anymore; it’s a strategic advantage. It allows companies to anticipate and reduce risks, turning their endpoint system into a strong security asset. This holistic approach changes devices from potential weaknesses into key parts of a robust and resilient security ecosystem.
Your Practical Roadmap To Endpoint Management Success
So, we’ve covered a lot of ground on endpoint management. Now, let’s talk about how to actually put it all into practice. This section is your guide to evaluating your current setup, choosing the right solutions, and making the transition smoothly. Think of it as planning a kitchen remodel—you wouldn’t start tearing out cabinets without a solid plan, right?
Assessing Your Current Capabilities: An Honest Look
Before diving into shiny new solutions, it’s crucial to take stock of where you currently stand with endpoint management. This isn’t about finding faults, but about establishing a clear starting point. Ask yourself these key questions:
- Visibility: Do you have a good grasp of the devices connecting to your network? Can you easily check their status and software versions?
- Control: How are you handling software updates and security policies? Is it a manual, time-consuming effort, or is it automated?
- Security: How confident are you in your current security posture? Are you constantly reacting to threats, or are you proactively preventing them?
- Cost: What’s your current endpoint management spend, encompassing software, hardware, and IT support?
By honestly answering these questions, you’ll pinpoint areas for improvement and direct your resources where they’ll have the biggest impact. This groundwork makes choosing a solution that truly meets your needs much easier.
Selecting the Right Solution: Finding the Perfect Fit
Picking the right endpoint management solution is a bit like choosing the right tool for the job – a hammer isn’t much use when you need a screwdriver. Consider these factors:
- Needs: What specific requirements does your organization have? Do you need basic device tracking, or are you looking for advanced security features like threat detection and response?
- Budget: Let’s be realistic, what can you afford? It’s about balancing the cost of the solution against the potential cost of not having a robust system in place.
- Scalability: Can the solution grow with your organization? Choose a solution that not only handles your current needs but also anticipates future expansion.
- Integration: Does it play nicely with your existing systems? You want a solution that simplifies things, not creates new integration headaches.
Planning Your Implementation: A Smooth Transition
The success of any implementation hinges on thorough planning. Here’s how to make the transition as seamless as possible:
- Phased Rollout: Don’t try to boil the ocean. Begin with a small pilot group, gather feedback, and then gradually expand to the rest of the organization.
- Communication: Keep everyone in the loop throughout the entire process. This minimizes disruptions and encourages smooth adoption.
- Training: Make sure your users have the training they need to effectively use the new system. This empowers them and reduces frustration.
- Support: Provide ongoing support to address any questions or issues that pop up. This fosters confidence and sets the stage for long-term success.
By taking these steps, you’re creating a practical, realistic plan tailored to your organization. This allows you to justify the investment, track your progress, and build a system that adapts as your business evolves.
How Tanium Reinforces the Endpoint Management Journey
Tanium uniquely combines real-time endpoint telemetry with actionable remediation, allowing IT and security teams to not only detect vulnerabilities but instantly act on them at scale.
Unlike legacy tools that operate with data delays and partial visibility, Tanium provides a single source of truth across endpoints — a vital capability in the era of remote work, ransomware, and hybrid infrastructure. This empowers organizations to go beyond passive monitoring and move toward active control, policy enforcement, and automated threat response — all from one unified platform.
Tanium Platform Overview
Tanium + Zero Trust Security
Some basics on zero trust from the experts:
How it is done now.
Tanium for Visibility and Control
This Tanium YouTube series dives deep into how Tanium provides real-time visibility and unified control across all endpoints — empowering IT and security teams with unparalleled insight and actionability. From discovery and inventory to configuration and remediation, this playlist is essential viewing for any organization modernizing their endpoint strategy.
What is Autonomous Endpoint Management (AEM)?
Autonomous Endpoint Management (AEM) represents the next evolution in endpoint strategy — where endpoints not only report issues, but intelligently resolve them with minimal human intervention. Tanium’s AEM capabilities allow organizations to automate detection, diagnosis, and remediation across large-scale networks, driving operational efficiency and security resilience. This is especially critical in environments with distributed workforces and ever-evolving threats.
Watch this video to learn how Tanium is pioneering the future of AEM:
Ready to gain better control of your endpoints and boost your organization’s security? Explore DATA-NIZANT for expert insights and resources on AI, machine learning, and digital infrastructure. We offer the knowledge and tools to help you navigate the complexities of endpoint management and achieve your goals.


